Supported Tools
The Mappings Manager can work with outputs from many different tools (previously known as "plugins" in older Dradis versions); however, not all are supported in the same way. Check the list below to see which tools are included in the Mappings Manager, as well as to view a list of all available data sources and their associated fields.
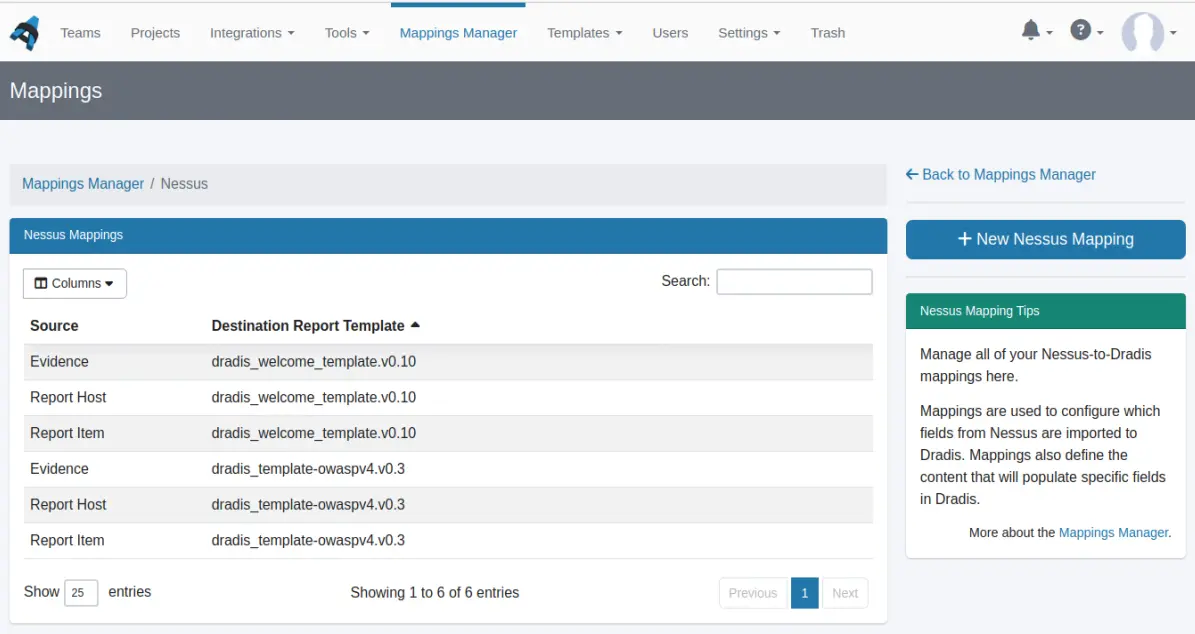
The Data Sources
The Mappings Manager allows you to choose a data source for every tool. Each tool has it's own set of data sources, which will populate a corresponding destination of the selected report template. For example, Nessus has 3 data sources: Evidence (for populating Evidence), Report Item (for populating Issues), and Note: Report Host (for populating Notes). You can pick the source to use from the dropdown.
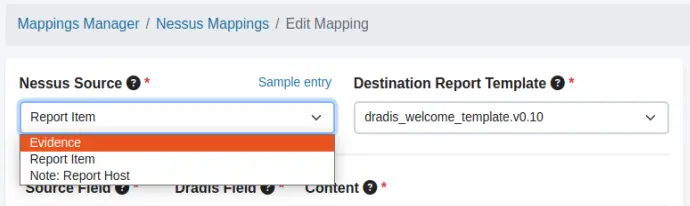
Create a mapping for each data source separately to achieve the exact output you need for your report template. More details on the specifics of integration with your report template will be provided later in this guide.
On upload, Dradis uses the plugin_id field (an automatically created field containing the unique ID from each tool) to create new Issues. If one Issue appears more than once in a file, one Issue will be created with multiple instances of Evidence. If you upload more than one file from the same tool, and the same Issue is present in multiple files, the first tool upload will define the severity of the Issue.
The Fields
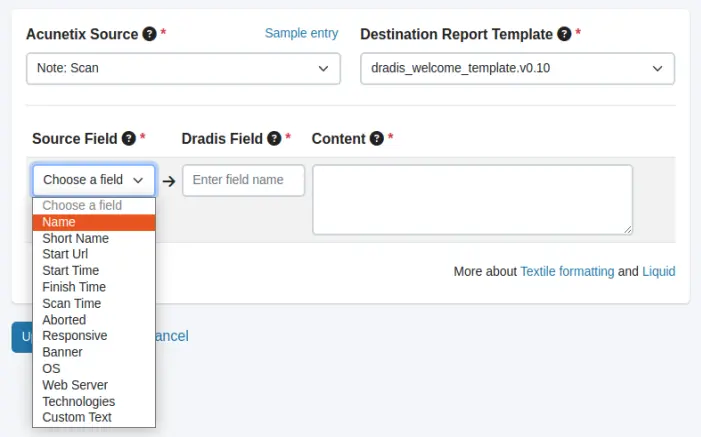
Each tool provides a list of fields that can be automatically imported into your mapping. Click on Choose a field to view a list of all the fields supported by the tool for that particular data source.
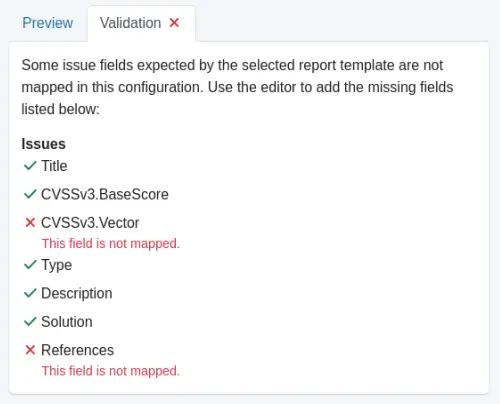
You can also check the fields you have mapped against your report template properties by selecting the Validation tab on the right side.
The combination of chosen data sources and the their mappings takes your uploaded tool output and creates a new Issue, Evidence, or Note in Dradis, customized exactly how you need it.
What does this mapping create when I upload my file?
You'll notice that each of the Supported Tools has a different naming convention for the different data sources. These names match up with the field names within the different tool outputs. For example, the Nessus Report Item data source corresponds to the data available in the ReportItem tags in the .nessus file.
Dradis::Plugins::Acunetix
The Report Item data source defines Issue fields.
The following fields are available:
name
module_name
severity
type
impact
description
detailed_information
recommendation
request
response
cvss_descriptor
cvss_score
cvss3_descriptor
cvss3_score
cvss3_tempscore
cvss3_envscore
cve_list
references
The Evidence data source defines Evidence fields.
The following fields are available:
details
affects
parameter
aop_source_file
aop_source_line
aop_additional
is_false_positive
request
response
The Evidence 360 data source defines Evidence fields for Acunetix 360 scans.
The following fields are available:
http_request
http_request_method
http_response
http_response_status_code
http_response_duration
The Vulnerability 360 data source defines Issue fields for Acunetix 360 scans.
The following fields are available:
name
type
url
description
impact
remedial_actions
exploitation_skills
remedial_procedure
remedy_references
external_references
severity
certainty
confirmed
state
owasp
wasc
cwe
capec
pci32
hipaa
owasppc
iso27001
cvss_vector
cvss_base
cvss_temporal
cvss_environmental
cvss31_vector
cvss31_base
cvss31_temporal
cvss31_environmental
Dradis::Plugins::AppSpider
The Evidence data source defines Evidence fields.
The following fields are available:
attack_config_description
attack_description
attack_id
attack_matched_string
attack_post_params
attack_request
attack_response
attack_user_notes
attack_value
attack_vuln_url
benign
original_value
original_response_code
The Vuln data source defines Issue fields.
The following fields are available:
attack_class
attack_score
attack_type
attack_value
capec
confidence
cwe_id
description
dissa_asc
html_entity_attacked
imperva_bl
imperva_wl
mod_security_bl
mod_security_wl
normalized_url
oval
owasp2007
owasp2010
owasp2013
owasp2017
pcre_regex_bl
pcre_regex_wl
recommendation
scan_date
snort_bl
snort_wl
statistically_prevalent_original_response_code
vuln_method
vuln_param
vuln_type
wasc
vuln_url
Dradis::Plugins::Brakeman
The Warning data source defines Issue fields.
The following fields are available:
warning_type
warning_code
fingerprint
message
file
line
link
code
render_path
location_type
location_class
location_method
user_input
confidence
Dradis::Plugins::Burp
The XML Evidence data source defines Evidence fields.
The following fields are available:
host
path
location
severity
confidence
request
response
detail
The XML Issue data source defines Issue fields.
The following fields are available:
background
detail
name
references
remediation_background
remediation_detail
severity
vulnerability_classifications
The HTML Evidence data source defines fields for the instances of Evidence that are created when you upload a Burp HTML re If you're uploading a Burp XML file, configure the Evidence data source instead.
The following fields are available:
confidence
detail
host
location
path
request
request_1
request_2
request_3
response
response_1
response_2
response_3
severity
Dradis::Plugins::CoreImpact
The Evidence data source defines Evidence fields.
The following fields are available:
agent_deployed
description
tried_to_install_agent
port
The Issue data source defines Issue fields.
The following fields are available:
title
agent_deployed
cve
description
port
tried_to_install_agent
Dradis::Plugins::Metasploit
Dradis::Plugins::Nessus
The Evidence data source defines Evidence fields.
cm_actual_value
cm_audit_file
cm_check_id
cm_check_name
cm_info
cm_output
cm_policy_value
cm_reference
cm_result
cm_see_also
cm_solution
plugin_output
port
protocol
svc_name
severity
plugin_name
The Report Item data source defines Issue fields.
The following fields are available:
age_of_vuln
bid_entries
cve_entries
cvss3_base_score
cvss3_temporal_score
cvss3_temporal_vector
cvss3_vector
cvss_base_score
cvss_temporal_score
cvss_temporal_vector
cvss_vector
cwe_entries
description
exploitability_ease
exploit_available
exploit_code_maturity
exploit_framework_canvas
exploit_framework_core
exploit_framework_metasploit
metasploit_name
patch_publication_date
plugin_family
plugin_id
plugin_modification_date
plugin_name
plugin_output
plugin_publication_date
plugin_type
plugin_version
port
protocol
risk_factor
see_also_entries
severity
solution
svc_name
synopsis
threat_intensity_last_28
threat_recency
threat_sources_last_28
vpr_score
vuln_publication_date
xref_entries
Dradis::Plugins::Netsparker
The Evidence data source defines Evidence fields.
The following fields are available:
extrainformation
rawrequest
rawresponse
url
vulnerableparameter
vulnerableparametertype
vulnerableparametervalue
The Issue data source defines Issue fields.
The following fields are available:
actions_to_take
certainty
classification_asvs40
classification_capec
classification_cvss_vector
classification_cvss_base_value
classification_cvss_base_severity
classification_cvss_environmental_value
classification_cvss_environmental_severity
classification_cvss_temporal_value
classification_cvss_temporal_severity
classification_cwe
classification_disastig
classification_hipaa
classification_iso27001
classification_nistsp80053
classification_owasp2013
classification_owasp2017
classification_owasp2021
classification_owasppc
classification_pci31
classification_pci32
classification_wasc
description
external_references
extrainformation
impact
knownvulnerabilities
remedy
remedy_references
required_skills_for_exploitation
severity
title
type
Dradis::Plugins::Nexpose
The Full Evidence data source defines Evidence fields.
The following fields are available:
content
id
port
protocol
status
The Full Vulnerability data source defines Issue fields.
The following fields are available:
added
cvss_score
cvss_vector
description
modified
nexpose_id
pci_severity
published
risk_score
references
severity
solution
tags
title
The Note: Full Scan data source defines the fields for a Note set to the Default category on the Nexpose Scan Summary Node.
The following fields are available:
end_time
name
scan_id
start_time
status
For a simple scan format, the Note: Simple port data source defines the fields for a Note set to the Default category for each Port associated with a specific Host (e.g. Node).
The following fields are available:
finding
id
Dradis::Plugins::Nikto
The Evidence data source defines Evidence fields.
The following fields are available:
request_method
uri
namelink
iplink
The Issue data source defines Issue fields.
The following fields are available:
id
request_method
osvdbid
osvdblink
references
description
uri
namelink
iplink
Dradis::Plugins::Nipper
The Evidence data source defines Evidence fields.
The following fields are available:
device_name
device_type
device_osversion
The Issue data source defines Issue fields.
The following fields are available:
title
cvss_base
cvss_base_vector
cvss_temporal
cvss_temporal_vector
cvss_environmental
cvss_environmental_vector
finding
impact
ease
recommendation
Dradis::Plugins::Nmap
Dradis::Plugins::OpenVAS
The Evidence data source defines Evidence fields.
The following fields are available:
port
description
The Result data source defines Issue fields.
The following fields are available:
threat
description
original_threat
notes
overrides
name
cvss_base
cvss_base_vector
risk_factor
cve
bid
xref
summary
insight
info_gathered
impact
impact_level
vuldetect
affected_software
solution
solution_type
Dradis::Plugins::Pentera
The Evidence template defines Evidence fields
The following fields are available:
evidence.found_on
evidence.port
evidence.protocol
evidence.target
evidence.target_id
The Issue template defines Issue fields
The following fields are available:
issue.insight
issue.name
issue.priority
issue.remediation
issue.summary
issue.severity
Dradis::Plugins::Qualys
The Vuln Evidence data source defines Evidence fields that are created when you upload a Qualys Vulnerability Management report.
The following fields are available:
cat_fqdn
cat_misc
cat_port
cat_protocol
cat_value
result
The Vuln Element data source defines Issue fields fields that are created when you upload a Qualys Vulnerability Management report.
The following fields are available:
number
severity
cveid
title
last_update
cvss_base
cvss_temporal
cvss3_base
cvss3_temporal
cvss3_version
pci_flag
vendor_reference_list
cve_id_list
bugtraq_id_list
diagnosis
consequence
solution
compliance
result
qualys_collection
The WAS Evidence data source defines fields for the instances of Evidence that are created when you upload a Qualys Web Application Scan report.
The following fields are available:
was-access_paths
was-ajax
was-authentication
was-ignored
was-potential
was-request_headers
was-request_method
was-request_url
was-response_evidence
was-response_contents
was-url
The WAS Issue data source defines fields for the Issue that are created when you upload a Qualys Web Application Scan report.
The following fields are available:
was-category
was-cvss_base
was-cvss_temporal
was-cvss3_base
was-cvss3_temporal
was-cvss3_vector
was-cwe
was-description
was-group
was-impact
was-owasp
was-qid
was-severity
was-solution
was-title
was-wasc
The Asset Evidence data source defines fields for the instances of Evidence that are created when you upload a Qualys Asset Scan report.
The following fields are available:
asset-cvss3_final
asset-cvss_final
asset-first_found
asset-last_found
asset-result
asset-ssl
asset-times_found
asset-type
asset-vuln_status
The Asset Issue data source defines fields for the Issue that are created when you upload a Qualys Asset Scan report.
The following fields are available:
asset-category
asset-cvss3_base
asset-cvss3_temporal
asset-cvss_base
asset-cvss_temporal
asset-impact
asset-last_update
asset-pci_flag
asset-qid
asset-result
asset-severity
asset-solution
asset-threat
asset-title
Dradis::Plugins::Saint
The Evidence data source defines Evidence fields.
The following fields are available:
port
severity
class
cve
cvss_base_score
The Vulnerability data source defines Issue fields.
The following fields are available:
description
hostname
ipaddr
hosttype
scan_time
status
severity
cve
cvss_base_score
impact
background
problem
resolution
reference
Dradis::Plugins::Veracode
The Evidence data source defines Evidence fields for the Flaw findings.
The following fields are available:
description
exploitlevel
issueid
line
mitigation_status
mitigation_status_desc
module
remediation_status
remediationeffort
sourcefile
sourcefilepath
The Issue data source defines Issue fields for the Flaw findings.
The following fields are available:
categoryid
categoryname
cweid
cwename
description
exploitlevel
issueid
line
mitigation_status
mitigation_status_desc
module
note
remediation_status
remediationeffort
severity
sourcefile
sourcefilepath
The SCA Evidence data source defines Evidence fields for the Software Composition Analysis findings.
The following fields are available:
file_name
file_path_value
library
library_id
mitigation
The SCA Issue data source defines Issue fields for the Software Composition Analysis findings.
The following fields are available:
cve_id
cve_summary
cvss_score
cwe_id
mitigation
severity
severity_desc
vulnerability_affects_policy_compliance
Dradis::Plugins::WPScan
Dradis::Plugins::Zap
Now that you understand how the Mappings Manager uses Tools, Data Sources, and Fields together to customize your findings, let's move on and integrate the Mappings Manager with YOUR report template.
Next help article: Integrating with your report template →