Without Enterprise-Grade Controls, You Risk:
- Failing client security assessments due to missing audit logs
- Losing government contracts that require NIST 800-53 compliance
- PCI-DSS violations if you can't prove MFA enforcement
- HIPAA penalties for inadequate access controls and audit trails
- Blocked procurement because your tool doesn't integrate with enterprise SSO
Enterprise Delivers What Auditors Need:
- SAML/LDAP/Okta integration - satisfy IA-2 (NIST) and PCI-DSS 8.3
- Mandatory MFA enforcement - meet multi-factor requirements across frameworks
- Complete audit logging - prove who accessed what, when (HIPAA 164.312(b), NIST AU-2)
- Role-based access controls - demonstrate least privilege (NIST AC-6, SOX ITGC)
- Self-hosted deployment - keep sensitive data behind your firewall
The safest choice
The peace of mind you're getting the features you need and the best service.
Enterprise |
Remediate |
Assess |
|
|---|---|---|---|
| Authentication and Identity | |||
| MFA with Azure | |||
| LDAP / Active Directory / Entra ID | |||
| Okta | |||
| SAML | |||
| Audit Logging | |||
| Support | |||
| Screen-share Troubleshooting | 10 sessions/month | 1 session/month | 1 session/month |
| Done-for-your Upgrades | |||
| Priority Support | |||
| Legal and Procurement | |||
| Vendor onboarding forms / portal | |||
| Pay by PO | |||
| Payment terms | NET30 | No | No |
| Minor EULA tweaks | |||
| Optional NDA | |||
| Seats included | 5 users | 1 user | 1 user |
Trusted by Security Teams Worldwide
More than 1,154 InfoSec teams in 75 countries have simplified their workflow with Dradis since 2007.
Enterprise SSO & MFA Out of the Box
Authenticate users through your existing identity provider - LDAP, Active Directory, SAML, Okta, Azure AD - no workarounds required.
Built-in Multi-Factor Authentication
Enforce OTP-based MFA across your entire instance - no third-party integrations required
Secure every account. Admins can enforce instance-wide MFA, and users get QR code setup with backup codes for easy onboarding.
- Easy setup with QR codes - scan with your authenticator app, get backup codes instantly
- Enforce MFA - protect password changes and admin functions
- Instance-wide enforcement - admins can require MFA for all users from the console
- Works with any OTP app - Google Authenticator, Authy, 1Password, and more

Self-Hosted, Behind Your Firewall
Keep sensitive pentest data on-premise or in your private cloud. Complete control over deployment, integrations, and upgrades - with no internet connectivity required.
- Meet data security requirements - comply with regulations that require on-premise or private cloud hosting
- Integrate with internal systems - connect to LDAP, Active Directory, and proprietary tools via API
- Air-gapped operation - deploy and upgrade without internet connectivity
- Your infrastructure, your rules - deploy on physical servers, VMs, or private cloud (AWS, Azure, GCP)
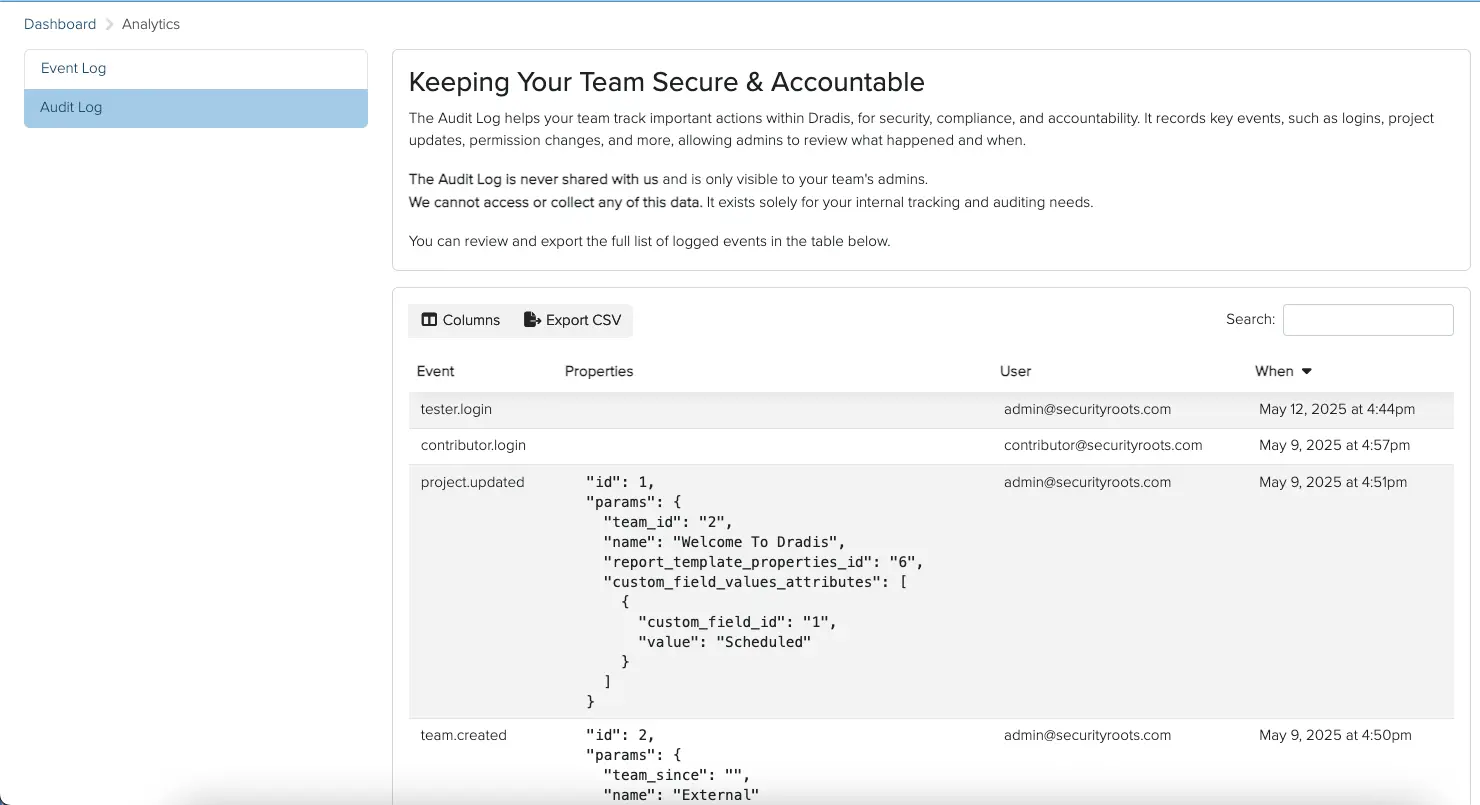
Audit Logging for Regulatory Compliance
Prove who changed what, when. Complete audit trails that satisfy FISMA, SOC 2, and internal compliance requirements
Track every critical action across your Dradis instance - project access, permission changes, user activity, and authentication events - with exportable logs and configurable retention.
- Complete project activity logs - creation, edits, exports, and deletions
- Permission and access tracking - know exactly who accessed what, and when
- Export to CSV - for compliance reports, incident response, or archiving
- Dedicated audit log UI - query and filter logs without accessing production data
Enterprise-Grade Security & Control
Built by security experts, integrated with your IT infrastructure, and designed to pass audits—without slowing down your team.
Security & Compliance Built In
- Developed by the authors of the UK CPNI guide on secure web applications
- Peer-reviewed and security-assessed before every release
- Automated vulnerability scanning in CI/CD pipeline
- Full-disk encryption for data at rest
- Integrate with LDAP / Active Directory for password policy enforcement
- Multi-factor authentication via Duo, Azure MFA, or built-in OTP
Deployment & Access Control You Own
- Role-Based Access Control (RBAC)—assign permissions by role
- Project-level permissions—users only see their assigned engagements
- Sync with your identity provider—LDAP, AD, or SAML
- Upgrade on your schedule—no forced updates or downtime windows
- Test in staging first—validate changes before production
- Air-gapped upgrades—no internet connection required
- Secure SSH management—no web admin panel needed
Priority Support & Enterprise Procurement
White-glove support and flexible procurement terms designed for enterprise buyers
Priority Support Package
Get direct access to our engineering team with guaranteed response times and hands-on assistance for deployment, upgrades, and troubleshooting.
- Dedicated success manager - your single point of contact
- Service Level Agreement (SLA) - guaranteed response times for critical issues
- Done-for-you configuration & upgrades - we handle the technical work
- Unlimited screen-share troubleshooting - get live help when you need it
- 98% GREAT ratings since 2020 - see our Happiness Report
All Enterprise customers also get: email and in-app support, access to community forums, and weekday chat support with our engineering team.
Enterprise Procurement Made Easy
We work with your procurement process - not against it. Get the contract terms and payment flexibility your organization requires.
- Pay by PO with NET30 terms - no credit card required
- Vendor onboarding forms and portals
- Custom contract terms - annual, multi-year, or custom agreements
- Optional NDA - we can sign yours or provide our standard agreement
- Minor EULA adjustments - work with your legal team on specific requirements
Need something else? We're flexible. Talk to our team about custom procurement requirements.
Seven Strategies To Differentiate Your Cybersecurity Consultancy
You don’t need to reinvent the wheel to stand out from other cybersecurity consultancies. Often, it's about doing the simple things better, and clearly communicating what sets you apart.
- Tell your story better
- Improve your testimonials and case studies
- Build strategic partnerships
Your email is kept private. We don't do the spam thing.