Automatically process findings from scanning tools like Burp, Nmap, Metasploit, NeXpose, and Nessus into a unified vulnerability database. Normalize findings across different tool formats, creating consistent vulnerability records that eliminate tool-specific inconsistencies.
Rules are chainable, easy to manage, and will make managing security findings a breeze.

You use multiple scanning tools and need a better way to manage the flood of output. Rules Engine lets you create custom rules for importing, categorizing, and combining findings from different tools. How much time will you save when you define how these tools work together - instead of drowning you in a flood of data?
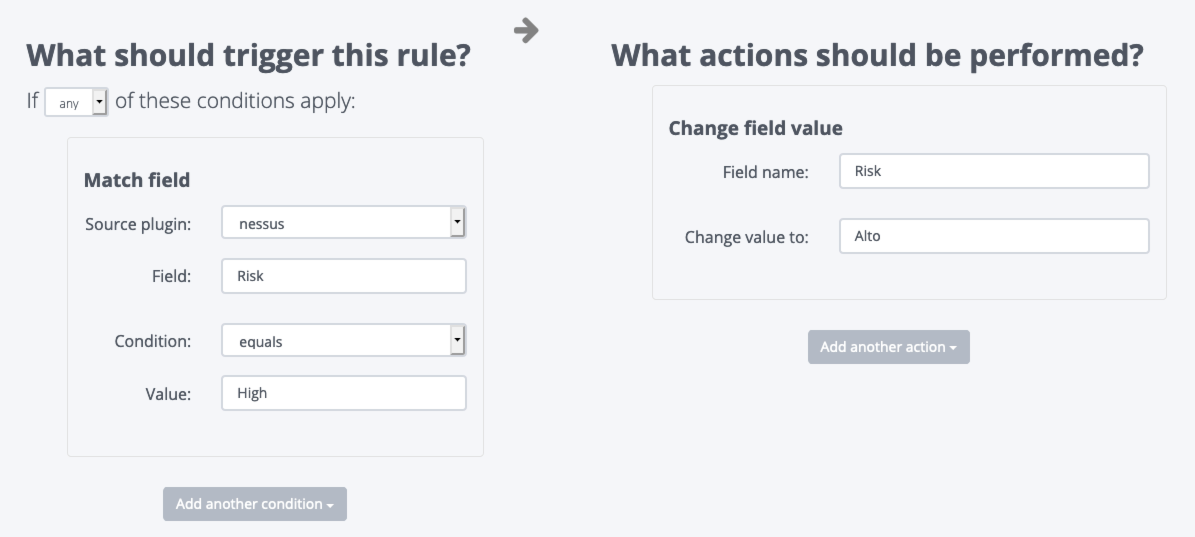
Automatically identifiy and merge vulnerabilities discovered by multiple scanners.
Reduce false positives, eliminate redundant findings, and create clean, actionable vulnerability reports without manual intervention. Save hours of manual vulnerability consolidation work.
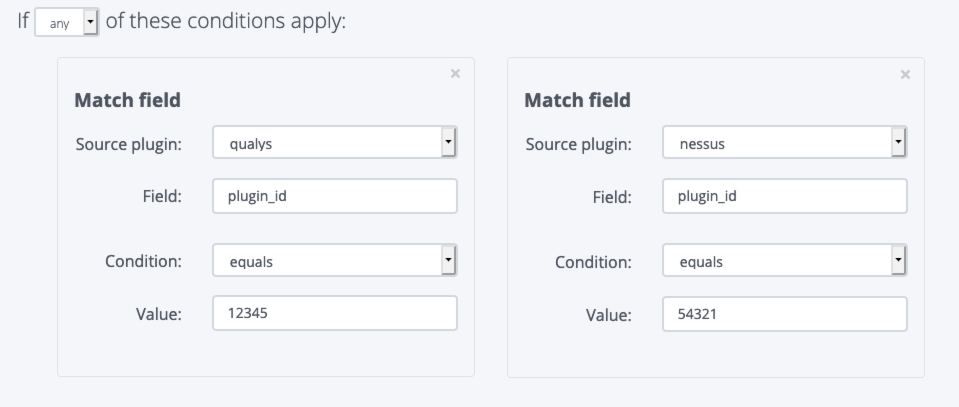
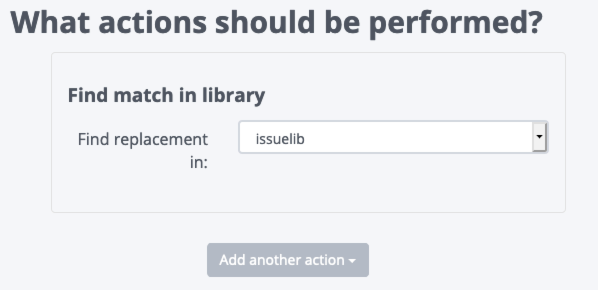
Pair with the Issue Library to replace vendor-provided vulnerability descriptions with your well-crafted write-ups. Use rules to tag findings based on your rating criteria for severity.
Your email is kept private. We don't do the spam thing.