Dradis Gateway turns static reports into live, interactive dashboards that clients can explore as your assessment progresses. No more sending PDFs for every update—Gateway gives clients real-time access to their findings, status changes, and remediation progress.
Clients log in securely to view updates, ask questions, and provide feedback, all from one centralized portal that's always up to date. It's the fastest way to keep stakeholders informed and engaged without extra effort from your team.
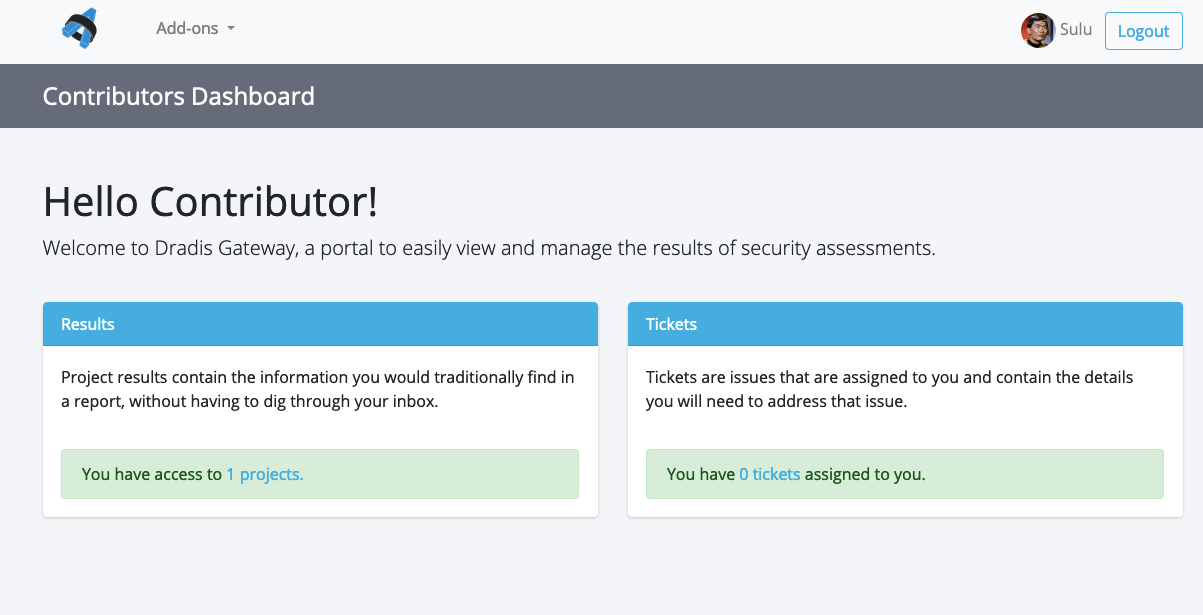
Collect scoping details, rules of engagement, or key contacts before the project even begins. With Gateway's built-in form builder, you can send customized questionnaires to gather everything you need to hit the ground running—no external tools required.
Forms can be reused across clients and tailored to different service types, helping standardize kickoff while keeping the experience personal.
Show off your work in a polished, fully branded portal that looks and feels like an extension of your team. Use Liquid and HTML to completely control how your findings, recommendations, and charts are presented to each client.
Style your content once and reuse the same layout across multiple projects. Gateway helps you look good—without extra effort.
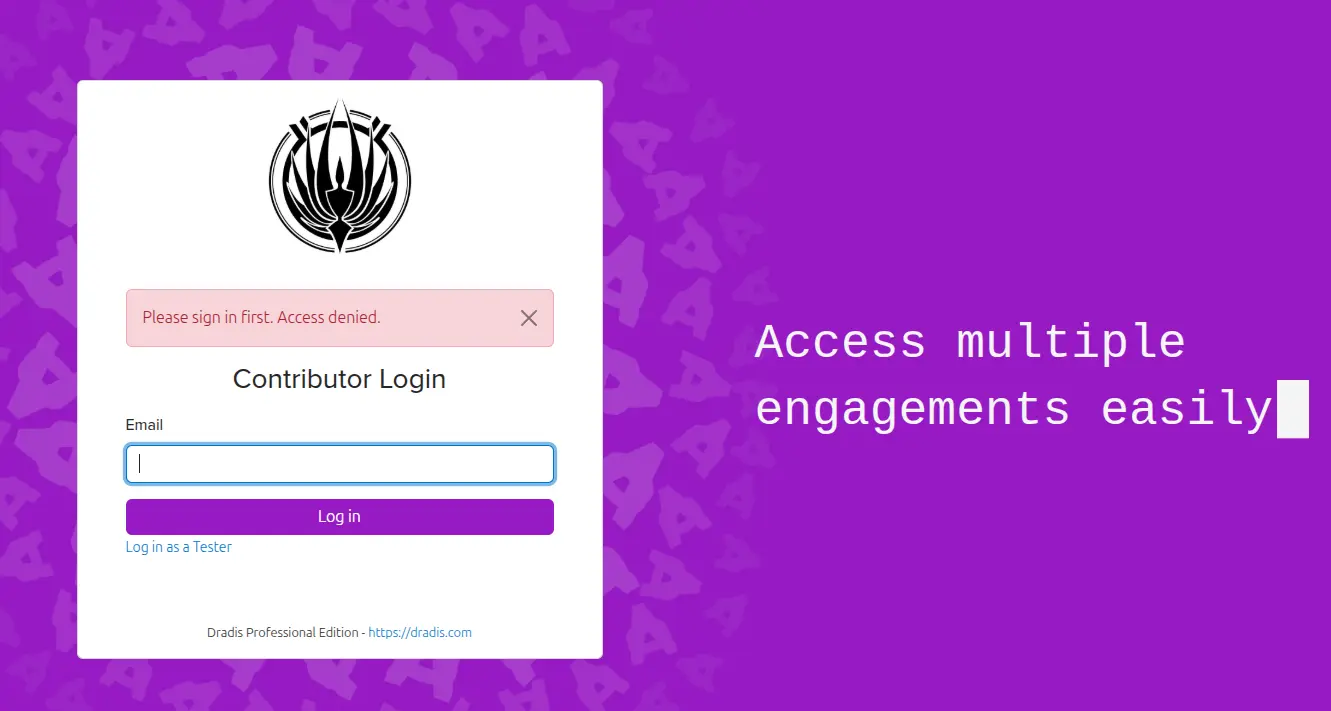
Dradis Gateway uses 2-step authorization to reduce the overhead of managing contributor access and unauthorized access. When a user with contributor access enters their email to log in they are emailed a link with a one-time sign-in token. No access to that email? No access to Dradis Gateway.
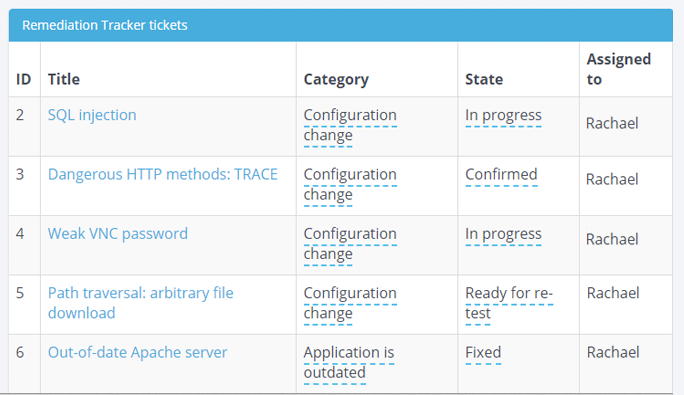
Accelerate remediation of security vulnerabilities when you pair Gateway with Remediation Tracker. Quickly create and assign detailed tickets from findings without leaving Dradis. Collaborate directly with system owners to remediate issues. Contributors can access assigned tickets, complete with all of the information and recommedations needed to close the gap between identification and resolution of an issue.
Contributor requests, remediation progress, and project completions can trigger automated actions across your security stack. Webhooks allow you to react to Gateway events in real time — creating SOAR tickets, posting Slack alerts, updating your billing system, or syncing remediation status to ServiceNow or Jira without manual hand-offs.
Keep your clients, security team, and operations team all in sync automatically. When a client submits a new project through Gateway, a webhook can kick off your internal onboarding workflow instantly.

Contributors, a new type of Dradis user, are given access to view and interact only with the project(s) they have explicit permissions for and the results of those projects. You are in full control of what is shared and who it is shared with. Best of all, contributors are unlimited and don't count against your Dradis license.
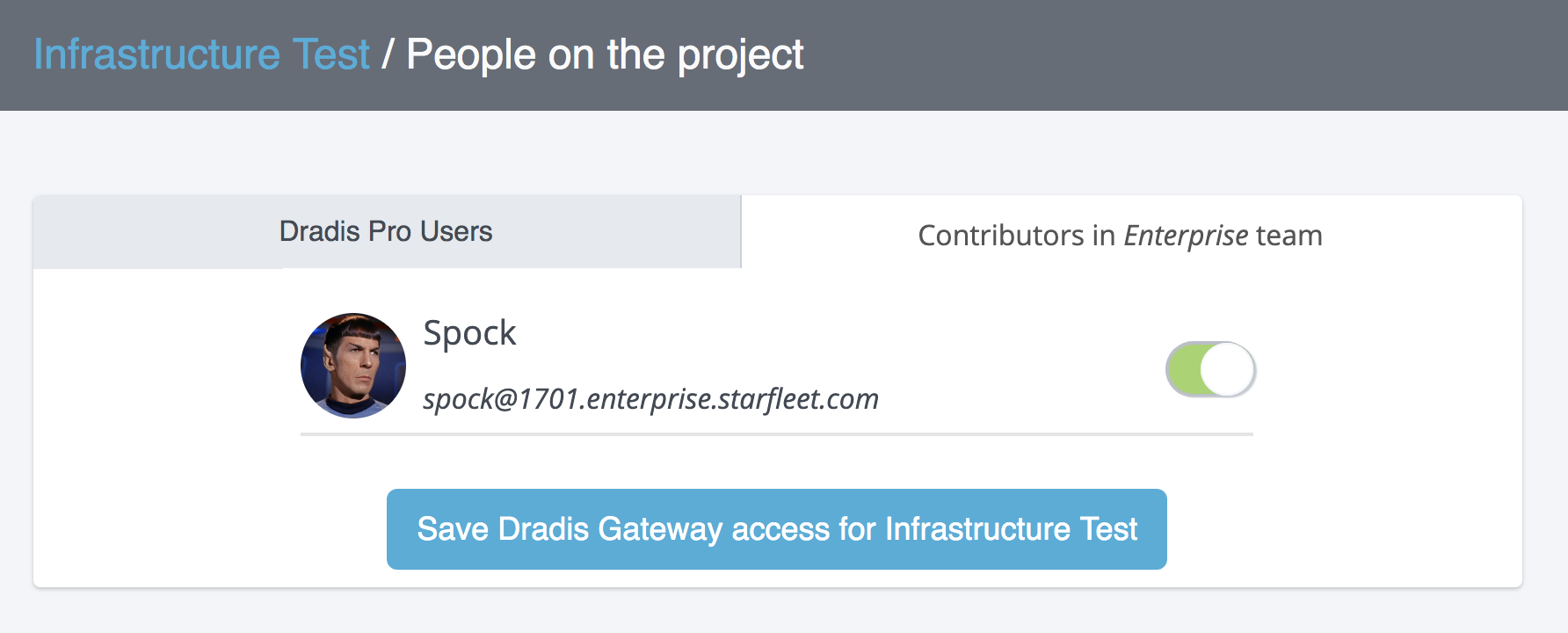
Your email is kept private. We don't do the spam thing.