When the WPScan team approached us in late 2019 offering to create an integration for Dradis, we were excited to work together. What goes together better than a WordPress security scanning tool and an easy way to turn those findings into a customized report? Maybe chocolate and peanut butter, but the Dradis WPScan integration is much more likely to result in a more secure website.
WordPress powers 35% of the Internet’s websites from hobby blogs to Fortune 50 companies. WordPress’ ease of use, well-established community, and extensive plugins offerings (55,457 as of this post) make it an attractive option for creating a presence online. Unfortunately, these same charms also make WordPress an easy and frequent target for attack.
In 2011, while investigating his own blog’s security, Ryan Dewhurst created a script that combined testing for WordPress’ vulnerabilities into a single tool. This script, now WPScan, enumerates usernames, plugins, and themes, performs brute force password attacks, and identifies the version of WordPress on a target.
WPScan contributors went on to create WPVulnDB to manage the ever-growing list of known WordPress vulnerabilities in an online database. When used together, WPScan and WPVulnDB API provide realtime detailed vulnerabilities and recommendations in your scan results.
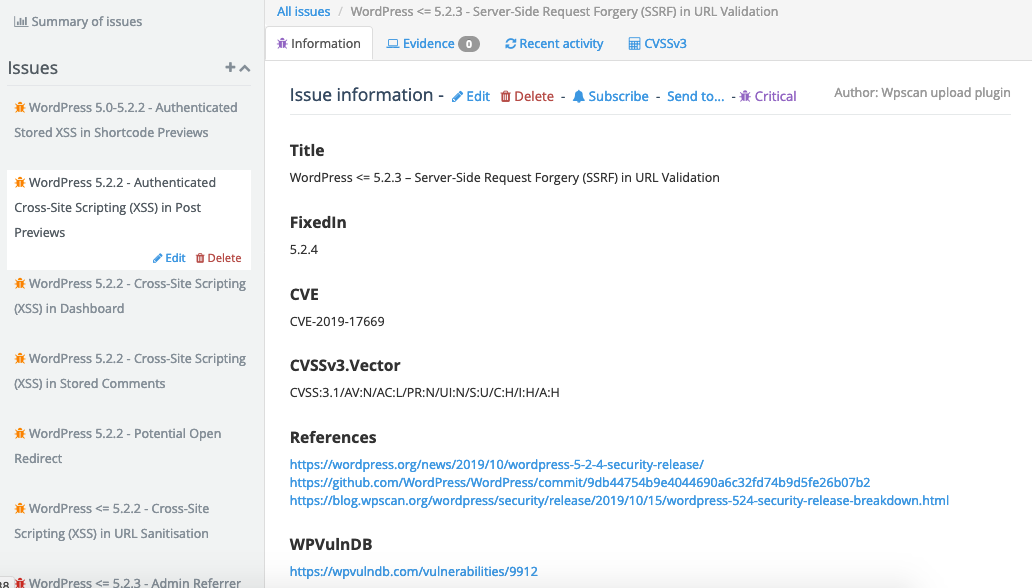
This new Dradis WPScan integration makes it a snap for you to import the results of your WPScan directly to a Dradis Project. Each target maps to a node within your Dradis project, any vulnerabilities found in a plugin, theme, or setup become Dradis issues, and when evidence is available – like a list of enumerated usernames – it is pulled into Dradis as evidence.
Ready to get started with Dradis and WPScan?
The steps to add the Dradis WPScan integration to Dradis CE or Dradis Pro are similar for both editions.
- Add or edit the
Gemfile.pluginsfile. The file locations for each edition is listed below- Dradis CE: top-level Dradis CE directory
- Dradis Pro:
/opt/dradispro/dradispro/shared/addons/- This file should be symlinked to
/opt/dradispro/dradispro/current/
- This file should be symlinked to
- Append
gem 'dradis-wpscan', github: 'dradis/dradis-wpscan'to the file - Save
Gemfile.plugins - $ bundle install
- Restart Dradis
- 🎉 All done!
If you run into any snags with the process, reach out on the community forums, the CE or Pro Slack workspaces, or directly to support.
TL/dr: Import WPScan findings into Dradis with the new Dradis WPScan integration